The OWASP Foundation has released the 2025 edition of its Top 10. If you're not familiar, the OWASP Top 10 is an industry standard for understanding the biggest risks in application security. Tracking how it changes over time tells us a lot about where we're improving as a security industry and where we still have room to grow.
Built in partnership with OWASP
We contributed to the OWASP Foundation on this release, sharing what we've learned through our security research. This included insights derived from our dataset of 127M security findings, 340k repositories, and 13k organizations.
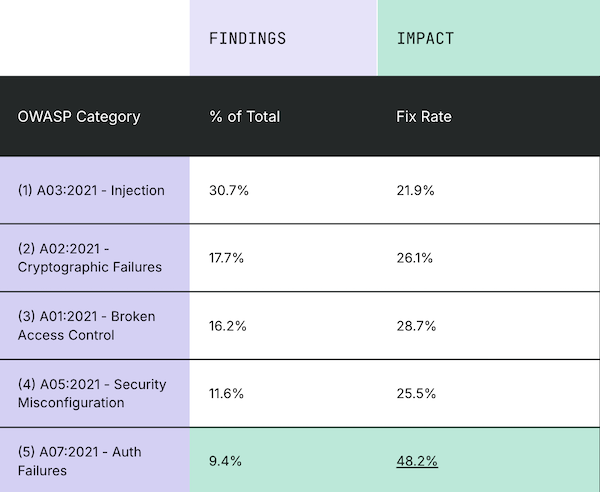
Here's a sample analysis of the findings and fix rate among the 2021 rules:
The team at OWASP spends tireless hours working with the security community to keep this list current and meaningful. They analyze data from hundreds of thousands of applications, gather input from practitioners worldwide, and distill it into guidance that shapes how organizations approach AppSec. They're great security-minded folks, and their commitment to keeping this resource free makes the entire ecosystem safer. It's an honor to work with them, and we hope to continue doing so for years to come.
The highlights
The 2025 edition includes two new categories:
Software Supply Chain Failures (#3) is new, expanding on the previous "Vulnerable and Outdated Components." It now covers the entire supply chain: compromised dependencies, malicious packages, tampered builds, insecure updates.
Mishandling of Exceptional Conditions (#10) is also new. Poor error handling, verbose error messages leaking data, systems that crash unpredictably.
Server-Side Request Forgery (SSRF) got rolled into Broken Access Control (#1). SSRF is fundamentally an access control problem, and this consolidation reflects that.
Together, these changes signal a growing trend that many of us have felt in the industry: software security is moving beyond just the code you write to include the entire software development lifecycle.
For a full breakdown of the new OWASP Top 10, check out the official report.
Semgrep rules are updated
We've updated all 4,000+ Semgrep rules to use the new OWASP Top 10 mappings. Our community and customers can now see exactly how the vulnerabilities they're finding map onto OWASP category risk.
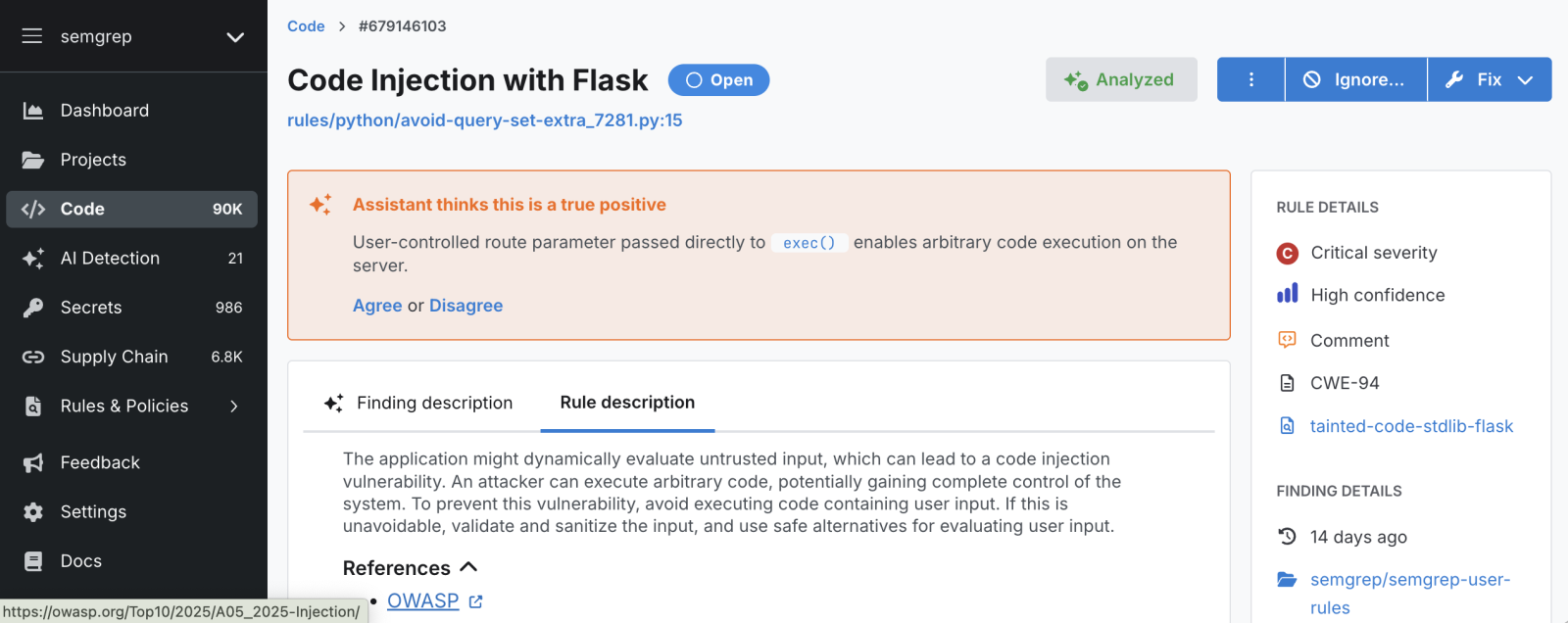
You'll find the mappings defined within each rule:
Explore the updated rules in the Semgrep Registry or you'll find them listed in resources related to your findings from the Semgrep AppSec Platform.