We're very excited to introduce the industry's first reachability analysis for PHP. One of the original languages used to power the web, PHP still remains in extensive use as a server-side language; over 70% of websites depend on it according to a report by W3Techs.
Semgrep’s reachability analysis helps dramatically reduce the noise of SCA vulnerability alerts. Available across 12 programming languages including PHP, reachability analysis determines not only if your code includes a dependency with a known vulnerability, but also if your code executes the vulnerable parts of the package in a vulnerable way. Security teams can use this analysis to automatically notify developers on PRs (or optionally fail builds) only on vulnerabilities that are reachable. See this blog post for more background on Semgrep’s reachability analysis.
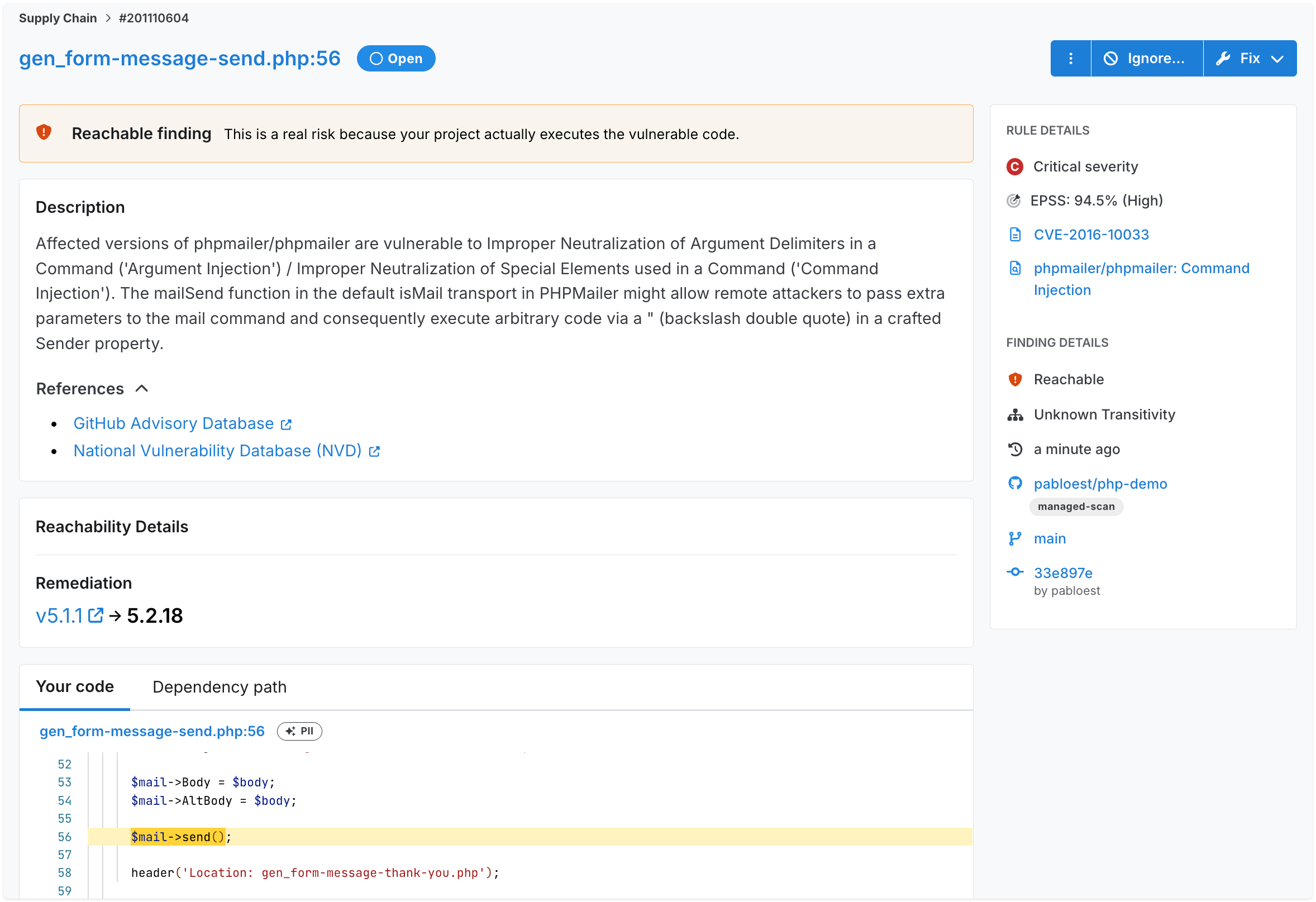
Here’s an example of how reachability works in practice. CVE-2016-10033 describes an injection vulnerability in which an attacker could manipulate PHPMailer and execute arbitrary code. This is done by crafting a malicious email address that contains injected parameters that are then subsequently handled by PHPMailer’s mail() function. While PHPMailer is a large library that can perform many email-related tasks, it’s only the mail() function that is subject to this attack.
Semgrep Supply Chain’s reachability analysis not only determines if your application code uses a vulnerable version of PHPMailer (versions before 5.2.18 for this CVE), but also if your code actually executes the vulnerable function, mail().
Below is a screenshot of a project with code affected by this vulnerability. Semgrep Supply Chain indicates the vulnerability is reachable and also displays the affected line of application code identified during the scan.
Now available in public beta, Semgrep Supply Chain covers PHP and the Composer ecosystem including support for critical severity CVEs published since 2017. As we progress towards general availability, we’ll also add support for high severity CVEs from May 2022 onwards.
July 2025 update: PHP reachability is now generally available! This means Semgrep Supply Chain includes reachability rules for all Critical-severity issues back to 2017 and High-severity issues back to May 2022 for packages used by customers.
If you're a current Semgrep Supply Chain customer, there's nothing you need to do to get PHP reachability analysis - if you have PHP code, the new reachability analysis will be part of your scans.
If you haven't tried Semgrep Supply Chain and have legacy (or modern!) PHP code, you can get started by simply creating an account and scanning a project. We’re excited to extend our reachability technology to the PHP world and would love to know what you think.